My Personal Take on the Maersk Case Study
Some images of Mr. Banks presentation were recently shared by Alon Refali from CyberTogether. I didn’t get to see the actual presentation, and I am not sure that a video will follow - so I took the liberty of writing down the slides so I could better comment on them.
The threat landscape has changed fundamentally
- the risk of us being caught up in Nation State activity is real
- these sort of cyber weapons are orders of magnitude more damaging than traditional malware
Prevention is unlikely to be an effective strategy, automated detection and response is key Online back up (standard) is no longer a safe approach Patching is necessary but insufficient Privileged access management takes on an even higher importance
for heavy industries, BCP & Crisis Management may need to be wider than asst focused
Skipping right to the conclusions, the struggle of the very large enterprise with security are tremendous. And as stated in the presentation, falling victim to Nation State conflicts will cause damages to your organization that current solutions are not dealing with well enough.
I think that there are some other options that can help limit and contain such issues, when assuming complete breach and network control by an adversary. Fast detection and automated response are key, but having a better baseline security for your server is just as important.
Server security is a difficult problem, and system hardening even more so - but assuming you’ve done your part - the blast radius of such malware will be significantly reduced - to the relativlely less protected systems (and endpoint devices). It’s not perfect - but it is easier to re-image laptops and printers than rebuilding your corporate application infrastructure.
Case Study: Lessons Learned from the NotPetya Cyber-Attack

Background to the malware: called NotPetya

“the superficial resemblance to Petya is only skin deep. Although there is significant code sharing, the real Petya was a criminal enterprise for making money. this [latest malware] is definitely not designed to make money. this is designed to spread fast and cause damage, with a plausibly deniable cover of ransomware”
Computer Security Veteran, The Grugg
- Tested on Ukranian power generation in December 2016, then US power generation in February this year
- targeted at Ukraine with a desire to disrupt a national holiday and delay tax payments
How it got in

- the default software for submitting tax returns in Ukraine is called MeDoc
- the software company that produces this was compromised (rogue employee) and “back doors” were put into the product giving the “hackers” access to all companies that used the software - including Maresk.
- the software automatically updates itself and in the June update it pulled the virus into our network
- Once on our network it looks to move from system to system, but it can not jump from one network to the other, meaning our customers and partners that connect to us remained software
What happened next
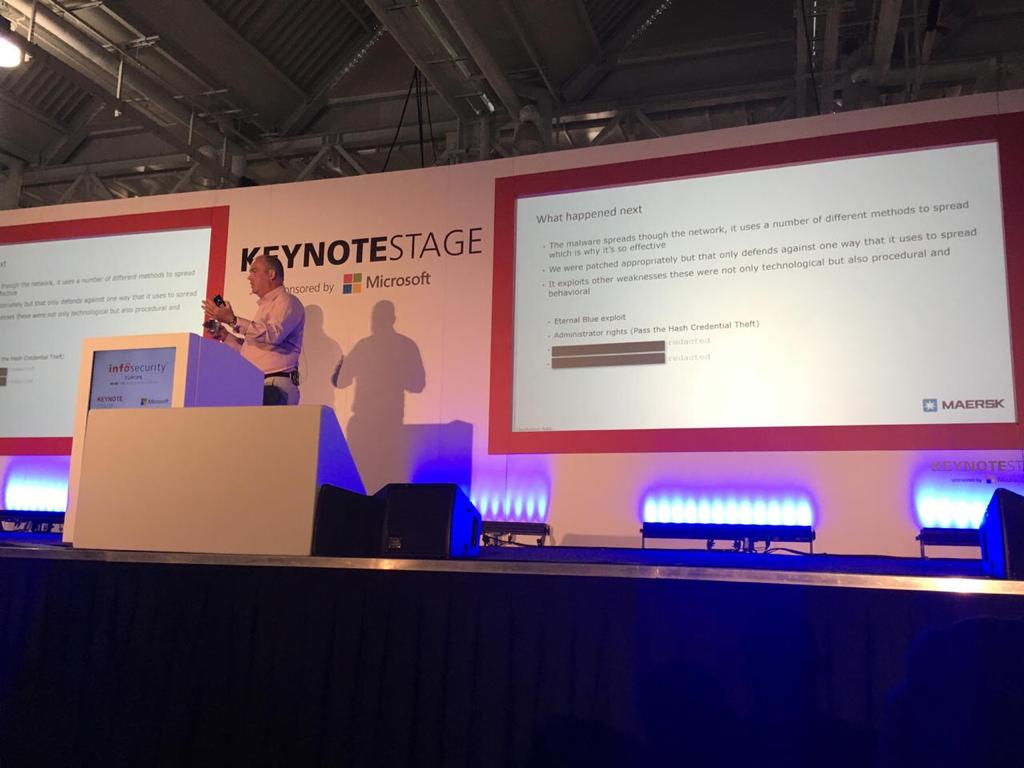
- the malware spreads through the network, it uses a number of different methods to spread which is why it’s so effective
- we were patched appropriately but that only defends against one way that it uses to spread
- it exploits other weaknesses there were not only technological but also procedural and behavioral
Attack Vectors: * eternal blue exploit * administrator rights (pass the hash, credential theft)
The Damages

IT Services
- DHCP and Active Directory badly damaged
- DHCP gives your computer an address
- AD is the phonebook
- Enterprise service bus destroyed
- vCenter (the thing that controls the cloud) damaged and unstable
End user Devices
- 49,000 laptops destroyed
- all print capability destroyed
- file shares unavailable
Applications and Servers
all our 1200 applications were inaccessible and approximately 1000 were destroyed. Data was preserved through backup but the applications themselves couldn’t be restored from backup as they would be immediately have been infected. The impact on servers was that 3,500 out of 6,200 servers were destroyed. Again they couldn’t be restored from back up due to reinfections.
What did we do: days 1-3

- implemented an F5 model for crisis management
- Deloitte assisted us with cyber forensics so we could reverse engineer the virus to understand how it worked
- decided to be as open as possible with the situation both internally and externally
- we designed new windows build - based on Windows 10 - that is less vulnerable to this specific virus
- we strengthened it as much as possible so it would be less vulnerable to other attacks
- we retrieved an undamaged copy of Active Directory
What did we do: days 4-9

- Built 2000 laptops
- rebuilt the active directory
- enabled core business process and systems
- we also spoke to the individual responsible for creating the malware
What did we do: day >9

- continues to work through the ever-growing list of applications
- 2 weeks in - all global applications restored
- 4 weeks in - all laptops rebuilt
Non-global applications, supporting non-global processes, have neem the most significant challenge in recovery
Industry wide learnings

The threat landscape has changed fundamentally
- the risk of us being caught up in Nation State activity is real
- these sort of cyber weapons are orders of magnitude more damaging than traditional malware
Prevention is unlikely to be an effective strategy, automated detection and response is key Online back up (standard) is no longer a safe approach Patching is necessary but insufficient Privileged access management takes on an even higher importance
for heavy industries, BCP & Crisis Management may need to be wider than asst focused
From slides presented by Adam Banks, Chief Technology & Information Officer, Maersk at InfoSec Europe 2019 (June 4-6, 2019)